What is Privileged Access Management? Know it All
- March 6, 2023

In a mobile-first environment, having unrestricted access to confidential data and critical operations is a recipe for colossal damage. Have you ever witnessed a floor executive installing new software on company devices, a project manager modifying system settings, or a receptionist configuring network connections and accessing critical business data systems?
The answer is an unequivocal no. It’s not just that their job roles do not necessitate the actions, but also because they lack the authority to carry them out.
What is Privileged Access?
Privileged access is a term used to describe the level of IT access that an individual has to an enterprise system or network. This level of access is typically reserved for top-level authority or those who need it in order to perform their job duties, such as system administrators or IT staff. A privileged access user has access to all sorts of confidential systems, data, and files that they would not normally have access to. They also have explicit permission to implement and execute actions that standard employees are denied.
Privileged Users: Privileged users are the users who have access to all information systems in the corporate network. They possess critical credentials to privileged accounts that provide direct access to corporate data, files, directories, and resources. Apart from the higher management and chief officers, they are typically assigned to IT heads and members such as network infrastructure administrators, system administrators, DevOps engineers, and database managers. The ability to access the system database, install software and programs, modify settings, configure policies, delete data, and remove users is what sets them apart from the standard users.
The Urgency of Privileged Access Management
Privileged identity theft is a cybersecurity threat in which an attacker obtains access to the login credentials of a privileged account and uses it to initiate unauthorized and unsafe activities. Cybercriminals frequently use this type of attack to gain access to critical systems, steal sensitive data, disrupt business operations, or cause other kinds of harm to an organization. Credentials to privileged accounts can be compromised through a variety of methods, including phishing attacks, malware, or social engineering tactics. Once the attacker has obtained the credentials, he or she can use them to impersonate the legitimate user, gain access to all confidential data, and conduct malicious activities without being detected. To prevent privileged identity theft, organizations should implement privileged access management (PAM) solutions that include multi-factor authentication, privileged session monitoring, and password vaulting to prevent privileged identity theft.
Privileged Access Management (PAM) is a security framework that is critical for any organization that wants to maintain the confidentiality and integrity of its digital assets.PAM ensures that high-level system access is reserved for only safe users with privileged accounts and is not hijacked by hackers and external users. It refers to the processes, policies, and technologies used to manage and control access to privileged accounts such as administrator accounts, service accounts, root accounts, and emergency accounts. This mechanism helps organizations protect and manage their sensitive data and systems of all types, including on-premises, cloud-based, and hybrid systems. PAM solutions are designed to work together to provide a comprehensive security solution that can be customized to fit the needs of any organization. It provides a centralized way to control who has access to what and helps to prevent unauthorized access and data breaches.
CubiLock is an Android device management solution that facilitates PAM and provides a unified device management platform for IT admins to mitigate the risks of mobility remotely.
It enables you to create a stress-free and secure work environment with the agility of privileged access management. The fundamental tools offered by CubiLock are:
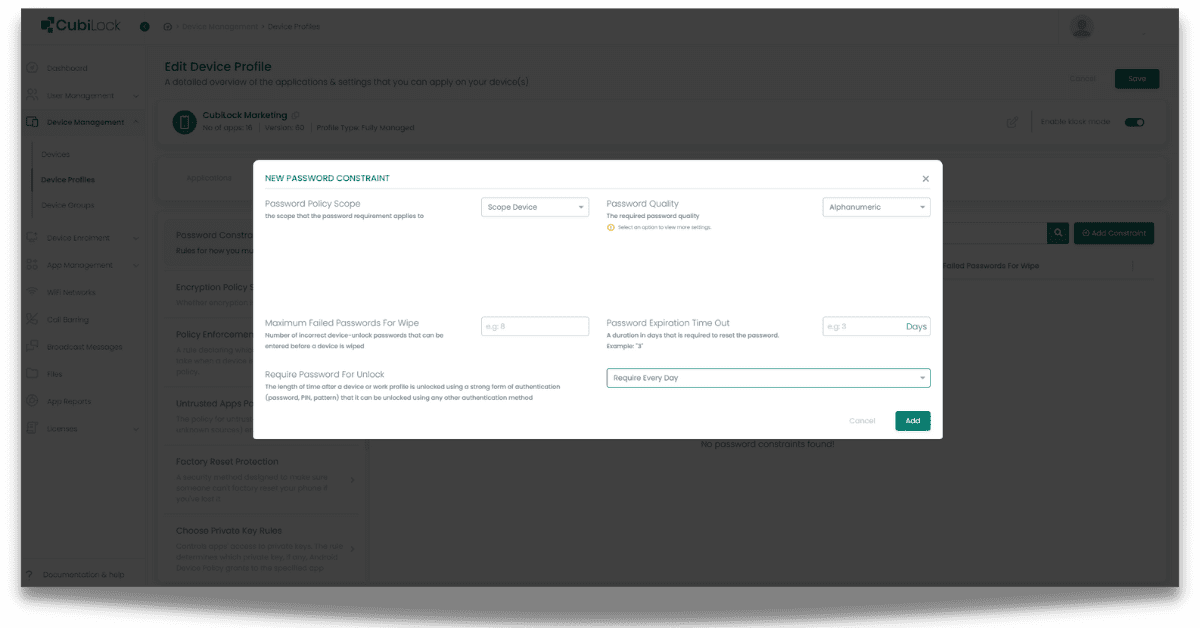
Encrypting passwords: CubiLock enforces password policies such as policy scope, minimum length requirements, complexity requirements, and expiration dates. It allows you to set the maximum number of failed password attempts before erasing all data from the device. It also supports the encryption of passwords stored on the device or transmitted over the network.
To encrypt passwords from the CubiLock dashboard:
From the CubiLock console,
- Go to the menu. Navigate to Devices Management > Device Profiles.
- Click on the three-dot menu next to the profile you want to update.
- Tap on the Update Profile from the drop-down menu to open in edit mode.
- Open Privacy Settings from the ribbon bar.
- From Password Constraints, Select +Add Constraints. This will open a pop-up to enable new password constraints.
- Choose Password Policy Scope and Set Password Quality (For e.g. alphanumeric).
- Click on Add to save your changes.
Configuring security policies: CubiLock can configure security policies such as disabling Bluetooth, WIFI, or USB connections, requiring data encryption, and enabling location tracking and remote data wipeout if a device is lost or stolen.
It can impose device restrictions such as restricting app installations or access to specific websites, as well as limiting access to device features such as the camera or microphone. These limitations can assist in preventing employees from using the device for personal purposes or exposing the device to cybersecurity breaches. These policies can be tailored to an organization’s specific security requirements.
Creating device work profiles: Work profiles can have their own set of security policies and restrictions, ensuring that work data is secure even when accessed via personal devices. Work profiles can also differentiate teams, projects, or simply job roles. The level of authority and restrictions can be configured according to the different needs of the work profiles. This way each work profile can have its own set of security policies and restrictions, giving organizations control over accessibility.
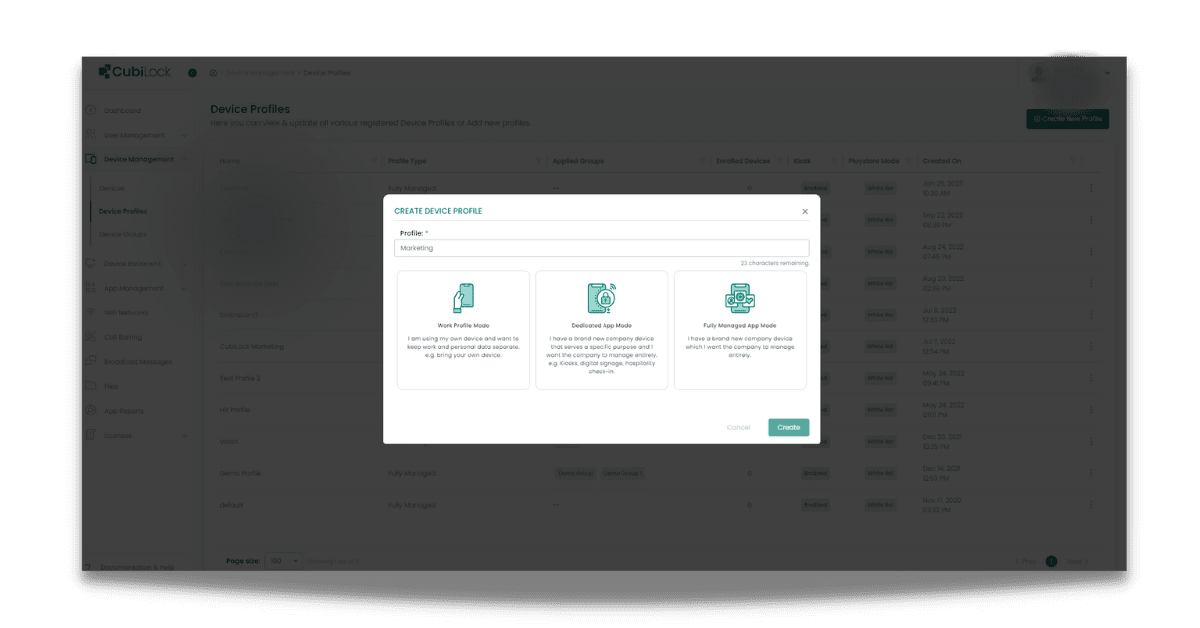
To create work profiles from the CubiLock dashboard:
From the CubiLock console,
- Go to the menu. Navigate to Devices Management > Device Profiles.
- Select +Create New Profile. From the pop-up box, enter the policy name and choose:
- Work Profile Mode: works best with BYOD policies.
- Dedicated App Mode: works best with brand-new corporate devices that are used for specific purposes.
- Fully Managed App Mode: works best with devices that are managed entirely by the company.
Takeaway
Cybercrimes have always been on the rise, but according to data, privileged identity theft has become a personal favorite of cybercriminals. The reason businesses need to secure privileged access is that it provides individuals with the ability to make changes to the system that could potentially compromise its security. By implementing privileged access management, businesses can help to prevent these types of attacks. Overall, PAM is essential for organizations that want to protect their digital assets, maintain compliance, and improve operational efficiency. And for this, CubiLock is a dynamic device management solution that offers android kiosk mode to tackle your security weaknesses, system vulnerabilities, and poor access management all under one roof.
Apart from being a true sushi enthusiast, Sadichha (Aka SSH) is a content writer and blogger at CubiLock. She is passionate to enchant everything boring and nitty gritty about technology through her writings for her readers to enjoy and learn from at the same time. When she is not at her desk crafting content, you can catch her occupied with her cat.